I’ve been wanting to setup brute for protection for SuiteCRM for a long time. Fail2Ban seems to be the best solution. There are snippets of how to do this all over the SuiteCRM forums but no really concise tutorial that I could find. So if you’re looking for a step by step tutorial on how to add Fail2Ban to SuiteCRM login, here’s a complete step by step guide.
This took hours of research and trial and error, so please if you have improvements or suggestions, please feel free to comment. I also ended up having to learn alot about firewalld service on linux and have listed some useful commands that you’ll need to get this all working.
Prerequisites
I’m doing this tutorial on a Centos 7 server with WHM/Cpanel. So your setup may be slightly different.
Step 1: Install Fail2Ban
The first step is to install Fail2ban on your CentOS 7 server. You can do this by running the following command as the root user in a terminal:
yum install epel-release
yum install fail2banStep 2: Configure Fail2ban
After installing fail2ban, you need to configure it to monitor the SuiteCRM login attempts. Fail2ban uses configuration files called jails to specify which services to monitor and how to respond to failed login attempts. You need to create a new jail for SuiteCRM.
Create a new file called suitecrm.conf in the /etc/fail2ban/jail.d/ directory using your preferred text editor. Add the following content to the file:
[suitecrm]
enabled = true
port = http,https
filter = suitecrm
logpath = /path/to/suitecrm/access.log
maxretry = 3
findtime = 300
bantime = 3600Replace /path/to/suitecrm/access.log with the actual path to your SuiteCRM access log file.
This configuration sets the maximum number of login attempts to 3, and if an IP address fails to log in more than 3 times within 300 seconds, it will be banned for 1 hour (3600 seconds).
Instruction on how to do this:
Open a terminal and connect to your CentOS 7 server using SSH:
Make sure you are running as admin
sudo suCreate a new jail for SuiteCRM:
touch /etc/fail2ban/jail.d/suitecrm.confOpen the suitecrm.conf file using a text editor:
nano /etc/fail2ban/jail.d/suitecrm.confThis command opens the suitecrm.conf file in the Nano text editor. You can use any text editor of your choice.
Add the following content to the suitecrm.conf file:
[suitecrm]
enabled = true
port = http,https
filter = suitecrm
logpath = /path/to/suitecrm/suitecrm.log
maxretry = 3
findtime = 300
bantime = 3600Replace /path/to/suitecrm/access.log with the actual path to your SuiteCRM access log file.
Note you cannot have the setting “Append after filename” set, or it wont find the log file. You also need to make sure the log file name matches.
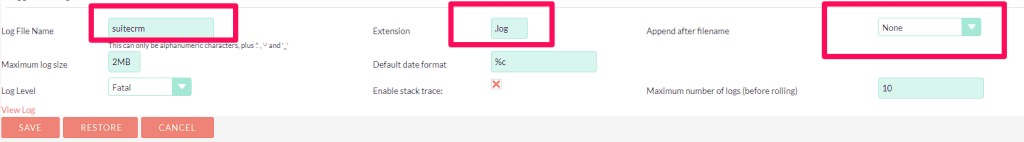
This configuration sets the maximum number of login attempts to 3, and if an IP address fails to log in more than 3 times within 300 seconds, it will be banned for 1 hour (3600 seconds).
findtime is the amount of time (in seconds) that Fail2ban will look back to determine if a particular IP address has exceeded the maximum login attempts. If an IP address has failed to login more times than the maximum allowed during the findtime period, Fail2ban will ban that IP address.
In this case, the findtime is set to 300 seconds, which means that Fail2ban will look back over the past 5 minutes to determine if an IP address has exceeded the maximum login attempts.
bantime is the amount of time (in seconds) that Fail2ban will ban an IP address if it has exceeded the maximum login attempts. Once an IP address is banned, it will be blocked from accessing your server for the duration of the bantime.
In this case, the bantime is set to 3600 seconds, which means that Fail2ban will ban an IP address for 1 hour if it has exceeded the maximum login attempts during the findtime period.
Note that these settings can be customized based on your specific needs. For example, if you have a high-traffic server or if you’re experiencing frequent login attempts from malicious sources, you may want to reduce the findtime and/or increase the bantime to better protect your server.
Save and close the suitecrm.conf file.
When you exit Nano after making changes to a file, it prompts you to save the changes before closing the editor. The prompt includes the message “Save modified buffer?” and gives you several options to choose from.
The options you’re seeing (“Dos”, “Mac”, “Append”, “Prepend”) refer to different line-ending formats that were used by different operating systems. You can select any of these options based on your preference, but the recommended format for Linux systems is Unix (or LF), which is the default format used by Nano.
To select the default format, simply press the Enter key without typing anything, or you can explicitly select the Unix format by typing U and then pressing Enter. After that, Nano will save the file with the changes you made and exit.
Step 3: Create Filter
Next, you need to create a filter for SuiteCRM. A filter is used to search the log files for failed login attempts.
Create a new file called suitecrm.conf in the /etc/fail2ban/filter.d/ directory using your preferred text editor. Add the following content to the file:
# Fail2Ban filter for suitecrm
#
[INCLUDES]
before = common.conf
[Definition]
_daemon = suitecrm
failregex = FAILED LOGIN:attempts\[.*.\], ip\[<HOST>\]
ignoreregex = This is a Fail2Ban filter for the SuiteCRM application. The [INCLUDES] section at the top is used to include a common configuration file (common.conf) that is shared across multiple filters.
The [Definition] section contains the actual filter rules.
The _daemon variable is set to suitecrm, which tells Fail2Ban which service to monitor for failed login attempts.
The failregex is a regular expression that matches the pattern of failed login attempts. In this case, the regular expression is FAILED LOGIN:attempts\[.*.\], ip\[<HOST>\].
The <HOST> tag is a special tag in Fail2Ban that matches any IP address. This regular expression matches the line in the log file that contains the string FAILED LOGIN:attempts, followed by any number of characters in brackets ([ and ]), followed by the string , ip[, followed by an IP address (matched by the <HOST> tag), followed by the string ].
The ignoreregex parameter is used to specify any lines that should be ignored by the filter. In this case, it is empty, which means that all lines not matching the failregex will be ignored.
Here are the SSH steps to do this:
Create a new filter for SuiteCRM:
touch /etc/fail2ban/filter.d/suitecrm.confThis command creates a new file called suitecrm.conf in the /etc/fail2ban/filter.d/ directory.
Open the suitecrm.conf file using a text editor:
nano /etc/fail2ban/filter.d/suitecrm.conf
This command opens the suitecrm.conf file in the Nano text editor. You can use any text editor of your choice.
Add the following content to the suitecrm.conf file:
# Fail2Ban filter for suitecrm
#
[INCLUDES]
before = common.conf
[Definition]
_daemon = suitecrm
failregex = FAILED LOGIN:attempts\[.*.\], ip\[<HOST>\]
ignoreregex = Save and close the suitecrm.conf file.
When you exit Nano after making changes to a file, it prompts you to save the changes before closing the editor. The prompt includes the message “Save modified buffer?” and gives you several options to choose from.
The options you’re seeing (“Dos”, “Mac”, “Append”, “Prepend”) refer to different line-ending formats that were used by different operating systems. You can select any of these options based on your preference, but the recommended format for Linux systems is Unix (or LF), which is the default format used by Nano.
To select the default format, simply press the Enter key without typing anything, or you can explicitly select the Unix format by typing U and then pressing Enter. After that, Nano will save the file with the changes you made and exit.
Step 4: Restart Fail2ban
After creating the jail and filter, you need to restart fail2ban to apply the changes.
systemctl restart fail2ban
Step 5: Test Fail2ban
You can test fail2ban by intentionally entering incorrect login credentials for your SuiteCRM instance. If you reach the maximum number of login attempts within the specified time, your IP address should be banned for the configured time.
Step 6: Check Fail2ban Status
You can check the status of fail2ban by running the following command:
fail2ban-client status suitecrm
This will show you the status of the SuiteCRM jail, including the number of banned IP addresses.
That’s it! You have successfully set up fail2ban to monitor and ban users who excessively fail to log in to your SuiteCRM instance.
How to Whitelist an IP
If you want to add an IP address for Fail2ban to ignore, you can add it to the ignoreip parameter in the jail.local file. You may have a static IP for your office and you don’t want one user locking out the whole company because they forgot their password. Here’s how you can do it:
Open the jail.local file using a text editor:
sudo nano /etc/fail2ban/jail.local
This command opens the jail.local file in the Nano text editor with root privileges.
Scroll down to the [DEFAULT] section and locate the ignoreip parameter.
Add the IP address you want to ignore to the end of the ignoreip parameter, separated by a space. For example, to ignore the IP address 192.168.0.100, add it to the end of the ignoreip parameter like this:
[DEFAULT]
ignoreip = 127.0.0.1/8 ::1 67.71.98.173Note that the ignoreip parameter may already have some IP addresses listed. Make sure to add the new IP address at the end and separate it from the existing addresses with a space.
Save and close the jail.local file.
Restart Fail2ban to apply the changes:
sudo systemctl restart fail2ban
After you’ve added the IP address to the ignoreip parameter and restarted Fail2ban, it will no longer ban that IP address even if it exceeds the maximum login attempts.
To add multiple IP addresses, you can add like this:
ignoreip = 127.0.0.1/8 ::1 192.168.0.100 192.168.0.101
Just put a space in between and add as many as you like.
Viewing the Contents of your Fail2Ban Log File:
Fail2ban has a log file that you can use to check for any errors or to see if Fail2ban is properly banning IP addresses. By default, the log file is located at /var/log/fail2ban.log.
You can view the contents of the log file by running the command:
sudo less /var/log/fail2ban.log
This will display the contents of the log file, and you can navigate through it using the arrow keys. If the log file is too large, you can use the grep command to search for specific entries. For example, if you want to search for all entries related to the SuiteCRM jail, you can run the command:
sudo grep "SuiteCRM" /var/log/fail2ban.log
This will display all log entries related to the SuiteCRM jail.
To exit the log file in terminal press the “q” key for quit.
Firewallcmd Problem
If you get something like this in your fail2ban log:
2023-04-10 15:50:37,999 fail2ban.actions [544]: ERROR Failed to execute ban jail 'suitecrm' action 'firewallcmd-rich-rules' info 'ActionInfo({'ip': 'xx.xx.98.173', 'fid': <function <lambda> at 0x7fb0ab49dc80>, 'family': 'inet4', 'raw-ticket': <function <lambda> at 0x7fb0ab49f2a8>})': Error banning xx.xx.98.173This suggests that your system does not have FirewallD installed or it is not running. You may need to install and start FirewallD on your system in order for Fail2ban to successfully ban IP addresses. Firewalld is what actually bans the IP from accessing your site.
You can run:
sudo systemctl status firewalldThis will check the status. If it’s not running you can run:
sudo systemctl start firewalld
Once the FirewallD service is running, you can try running the failed command again and see if it works. If you still encounter issues, you may need to check the FirewallD configuration to ensure that it is properly configured to allow Fail2ban to add rules.
You can also enable the firewalld service to start automatically at boot time with the following command:
systemctl enable firewalld
Once you activate the firewall, most likely all your ports are going to be blocked.
If you need to disable firewalld you can with the following commands:
systemctl stop firewalld
systemctl disable firewalldYou can allow incoming traffic on the ports that your website is using. By default, HTTP uses port 80 and HTTPS uses port 443. You can allow incoming traffic on these ports by running the following commands:
sudo firewall-cmd --zone=public --add-service=http --permanent
sudo firewall-cmd --zone=public --add-service=https --permanent
sudo firewall-cmd --reloadThis will add the HTTP and HTTPS services to the public zone and make the rules permanent, so they will persist after a reboot. The –reload option is used to apply the new rules.
You can also allow incoming traffic on specific ports if your website is using a non-standard port. For example, if your website is using port 8080, you can run the following command:
sudo firewall-cmd --zone=public --add-port=8080/tcp --permanent
sudo firewall-cmd --reloadThis will allow incoming traffic on port 8080/tcp and make the rule permanent.
Make sure to test your website after making these changes to ensure that it is accessible from the web.
You’ll probably also want to make sure Mail ports are open for IMAP and SMTP. To open the ports for IMAP (143 and 993) and SMTP (25, 465, and 587), you can use the firewall-cmd command in SSH listed below. As well consider what other ports you need to open ie: MySQL for external access to your DB.
sudo firewall-cmd --permanent --add-service=ftp
sudo firewall-cmd --permanent --add-service=ssh
sudo firewall-cmd --permanent --add-service=smtp
sudo firewall-cmd --permanent --add-service=pop3
sudo firewall-cmd --permanent --add-service=imap
sudo firewall-cmd --permanent --add-service=mysql
sudo firewall-cmd --permanent --add-service=submissionFor cpanel and WHM you will also need:
sudo firewall-cmd --permanent --add-port=2082-2083/tcp
sudo firewall-cmd --permanent --add-port=2086-2087/tcp
sudo firewall-cmd --permanent --add-port=2095-2096/tcp
sudo firewall-cmd --permanent --add-port=2086/tcpIMAP and SMTP SSL Ports
sudo firewall-cmd --add-port=993/tcp --permanent
sudo firewall-cmd --add-port=465/tcp --permanent
sudo firewall-cmd --add-port=587/tcp --permanentOnce you make all these changes, you’re going to want to reload the firewall. Always do this after you make changes.
firewall-cmd --reload
Finally, if you want to see what ports are open by firewalld you can use the following to see a list of open ports:
sudo firewall-cmd --list-portsSpecial Case for Godaddy
Godaddy servers need a port open for their managment system:
sudo firewall-cmd --permanent --zone=public --add-port=2224/tcp
Don’t forget to re-load the firewall after.
Nydus and Port 2224: Nydus refers to a pair of agent applications (nydus-ex and nydus-ex-api) running on your server that communicate with the server dashboard, providing resource metrics and performing server operations you’ve requested. The agent listens on port 2224.
To Unban an IP:
If you accidentally ban yourself or would like to unban an IP use the follwing:
sudo fail2ban-client set suitecrm unbanip <IP_ADDRESS>That’s it!
That’s everything I could think of to include in this compendium of Fail2Ban and SuiteCRM tutorial. Seems like a firewalld tutorial as well! If you have any ideas or additions, please comment or send me an email. I’d love to make this tutorial the best possible on the web.

